IntegraShield. The new guard protecting data security.
IntegraShield protects against unauthorized access to your personal data that can lead to significant breaches, distrust of corporate integrity and financial loss.
Cloud Market Expansion. As the market for cloud-based solutions and interoperability between systems continues to expand, breaches from unauthorized access have continued to grow. Don’t just react to data breaches, eliminate them with IntegraShield. Whether the data is consumer payment accounts, private healthcare information or privacy centric, IntegraShield is designed to limit and control external access.
IntegraShield’s tamper-proof design prohibits unauthorized access and enables notification of attempted modifications providing a forensic footprint for all transactions within the enterprise.
Monitor and control sensitive data and transactions in real-time with IntegraShield’s comprehensive dashboard.
IntegraShield features:
- Validates originating client request MAC address to a Shield controlled Access Control List
- Validates originating client IP address to a Shield controlled IP white table listing
- Validates public internet address against a Shield controlled blacklist
- Validates that Shield Client boxes are not tampered or altered
- Enhance security protocols eliminate Man-in-the-Middle (MITM) attacks securing “in-transit” data
- Each Shield Client has a security profile that aids us to prevent fraudulent activity as well as creating predictability results
- Utilizes 256-bit SSL/TLSv1.2 encryption alongside a SHA-256 byte message authenticated data stream
- Provides a complete set of statistical reporting and a customer specific dashboard for monitoring real-time traffic
Amazingly agile, incredibly simple.
- Dedicated hardware to control API access
- Each module uniquely configured to allow only verified external users
- Small footprint as well as rack mounted option
- High-performance encryption engine
- Tamper-proof monitoring
- Utilizes Intel® Next Unit of Computing (NUC) technology, Supermicro or BeagleBone technology depending on throughput requirements
- M2 security hardware, software and firmware
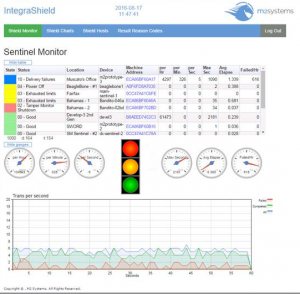
Operational Control and Monitoring. The IntegraShield Dashboard provides data security personnel and CISO’s with a fully-integrated console for monitoring and reporting. With proper credentials, users can access the console from any supported device and browser. Alerts and notifications can be easily customized based on operational requirements. Individual locations or enterprise aggregation of critical usage and security information is right at your fingertips.
IntegraShield Dashboard
Powered by M2 Systems
The IntegraShield Dashboard provides CISO, data security personnel, and operational staff with a fully-integrated console for monitoring and reporting. With proper credentials, users can access the console from any supported device and browser. Alerts and notifications can be easily customized based on operational requirements. Individual locations or enterprise aggregation of critical usage and security information is right at your fingertips.
- Transaction Activity Counts
- IP Address Activity
- MAC Address Transactions
- Application Programming Interface (API) Call Counts
- Transaction Response Times
- Graphical Reports and Charts in Real-time
- Robust Filtering Capabilities
At M2 Systems, we make data make sense. M2 Systems has a 30-year history of developing next generation software to successfully provide global systems solutions. M2 is a leading provider to Fortune 500 companies of both software licenses and cloud processing services in the healthcare and financials systems markets. M2 is uniquely qualified to develop solutions that protect against unauthorized access and data breaches.
Our industry-standard, cost-effective, tamper resistant hardware/firmware design provides a new approach to external access solutions. M2 is an experienced provider of PCI, PHI, and HIPAA compliant systems and services. IntegraShield’s encryption standards meet the FIPS140-2 federal certification. We understand the requirements and complexity of authenticating and controlling access to sensitive information. Unauthorized access to payment processing systems and electronic health information are the leading causes of financial fraud and identity theft.